For any person with considerable bitcoin holdings, a custody construction that features a unmarried level of failure will have to be discoverable as uninvited. If a pockets has a unmarried feature that—when misplaced or stolen—can manage to an everlasting lack of price range, later it’s just too unhealthy to imagine. No one needs to accumulation important wealth teetering at the fringe of emergency.
Person bitcoin holders have diverse gear to be had that may support let fall the chance of loss or robbery. In a prior article, we coated a few of these gear, highlighting changes repeatedly implemented to singlesig wallets. On the other hand, we additionally defined why those approaches fall shorten of doing away with unmarried issues of failure solely.
For a industry, executive, or alternative establishment that wishes to accumulation a bitcoin treasury, getting rid of unmarried issues of failure is not only a nice-to-have, however a prerequisite. The one custody fashions significance taking into account for those entities are ones that come with a threshold requirement to deliver to get entry to price range. A threshold requirement describes a construction that comes to a couple of, one by one tie elements, the place a subset of the ones elements are had to approve any withdrawal. That is the one method of accomplishing institutional-grade safety, with unmarried issues of failure eradicated utterly.
On this article, we’ll barricade tips on how to practice threshold safety the usage of 3 other forms: script multisig, Shamir’s unrevealed sharing (SSS), and multi-party computation (MPC). We’ll additionally dive into the tradeoffs related to every means, and the way an establishment can make a selection the most efficient setup to satisfy their wishes.

What’s multisig?
If you happen to aren’t certain what script multisig is, we advise trying out our previous article devoted to explaining how multisig wallets paintings and what they’re impaired for. As a snappy overview, a multisignature pockets comes to a couple of personal keys, and will also be configured in order that a particular quantity (threshold) of the ones personal keys are required to signal any transaction. The signatures will also be produced at other occasions and places, permitting every key to stay bodily separated. As soon as a threshold collection of signatures were produced, they may be able to be blended right into a unmarried bitcoin transaction in a position to spending the price range.
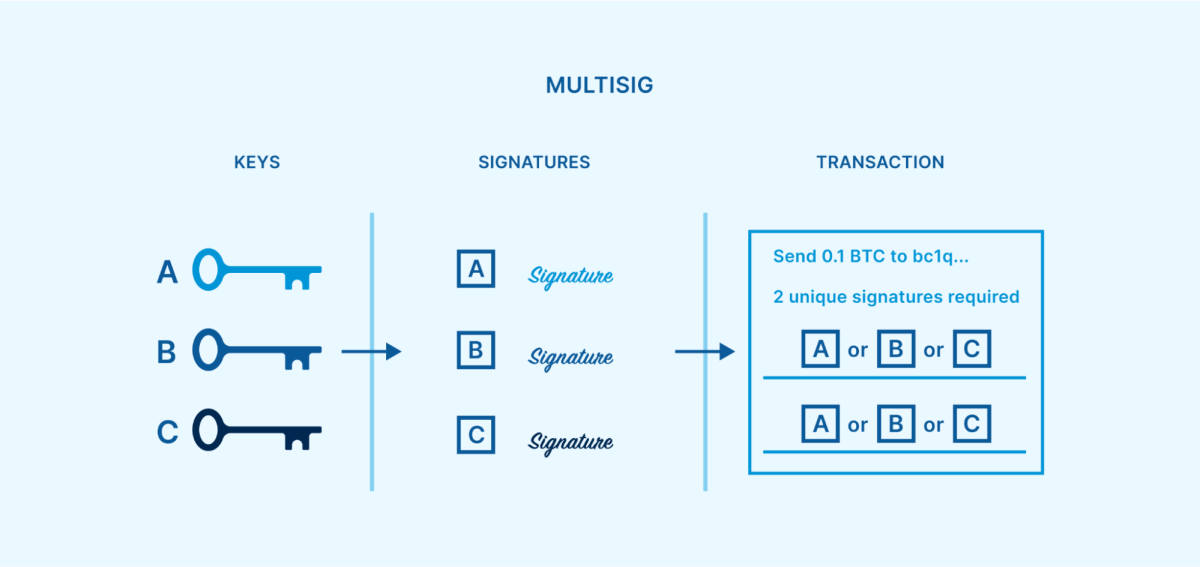
This quite easy method of making a threshold requirement is extremely efficient at doing away with all unmarried issues of failure. So long as the spending threshold is bigger than one however lower than the entire collection of keys, later any unmarried key can develop into misplaced, stolen or destroyed with out bitcoin changing into unrecoverable. The excess keys may signal a healing transaction transferring price range to a unused multisig setup.
Satoshi Nakamoto laid the groundwork for multisig when bitcoin used to be first spared, expecting that it generally is a widespread mechanism for securing price range. On the other hand, it wasn’t till the P2SH softfork in 2012 that multisig began to develop into a broadly impaired instrument. Multisig has since confirmed itself as a battle-tested safety type for greater than a decade, throughout a number of other deal with sorts.
What’s Shamir’s unrevealed sharing?
Shamir’s unrevealed sharing (SSS) is a unrevealed sharing set of rules that used to be evolved by means of famend cryptographer Adi Shamir in 1979. It may be impaired as in a different way of introducing a threshold requirement for shielding bitcoin. SSS lets in customers to fracture a key into a number of allotted “shares,” with just a positive threshold of the stocks had to reassemble the important thing. This will also be impaired to design quorums like 2-of-3 or 3-of-5, matching to multisig.
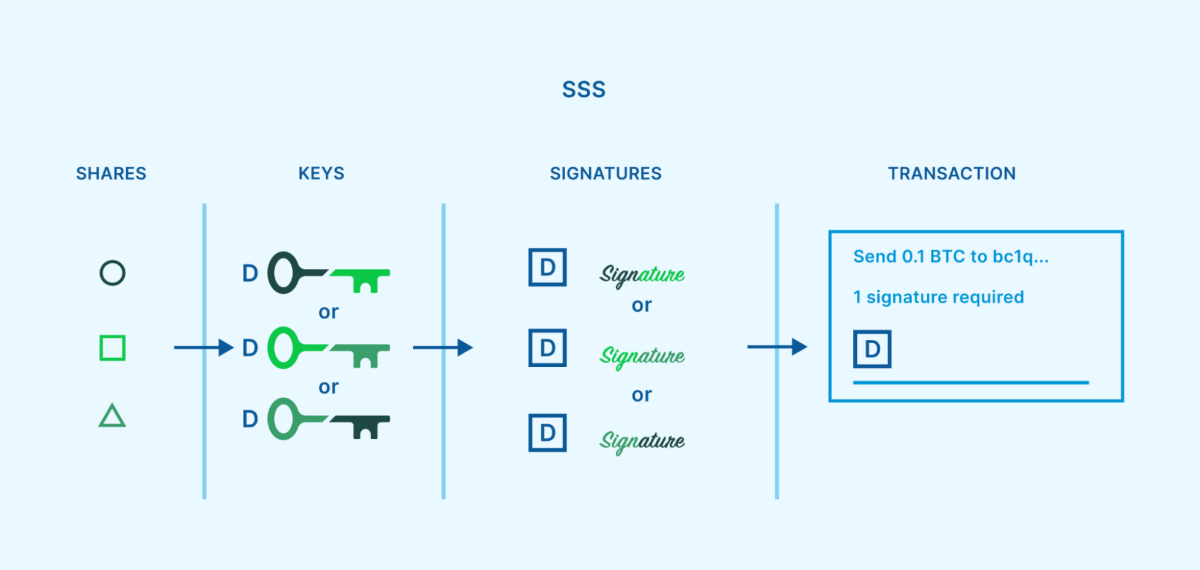
On the other hand, this means nonetheless ends up in unmarried issues of failure at positive cases all the way through its lifecycle. One instance is when the bottom line is to start with fracture up into SSS stocks. This operation is most often finished on a unmarried software at a unmarried day and playground. If an attacker compromises that software, the important thing year procedure or the proportion starting procedure, they’ve compromised the important thing. Some other instance is each time the person must reassemble the important thing to signal a transaction. A threshold collection of stocks will have to be introduced in combination, as soon as once more on a unmarried software at a unmarried day and playground, which an attacker may exploit.
A relatively easy and broadly impaired mode of enforcing SSS era for cryptocurrency custody is throughout the Shamir additional, evolved by means of Satoshi Labs in 2017. It may be discovered as an possibility in positive Trezor {hardware} pockets fashions.

What’s MPC?
MPC, or multi-party computation, is a subfield of cryptography that lines again to the Seventies. The purpose of MPC is to permit a couple of members to collectively carry out a computation, past every player’s contribution to the computation isn’t obvious to the residue of the crowd and subsequently can stay personal. This permits for a couple of events to collaborate in diverse contexts without having to believe every alternative.
When implemented to bitcoin custody, MPC comes to allotted “shares,” matching to SSS. On the other hand, not like SSS, the stocks don’t seem to be fracture from a personal key nor impaired to rebuild a personal key. Rather, a couple of events compute a unmarried signature without delay from a threshold in their stocks.
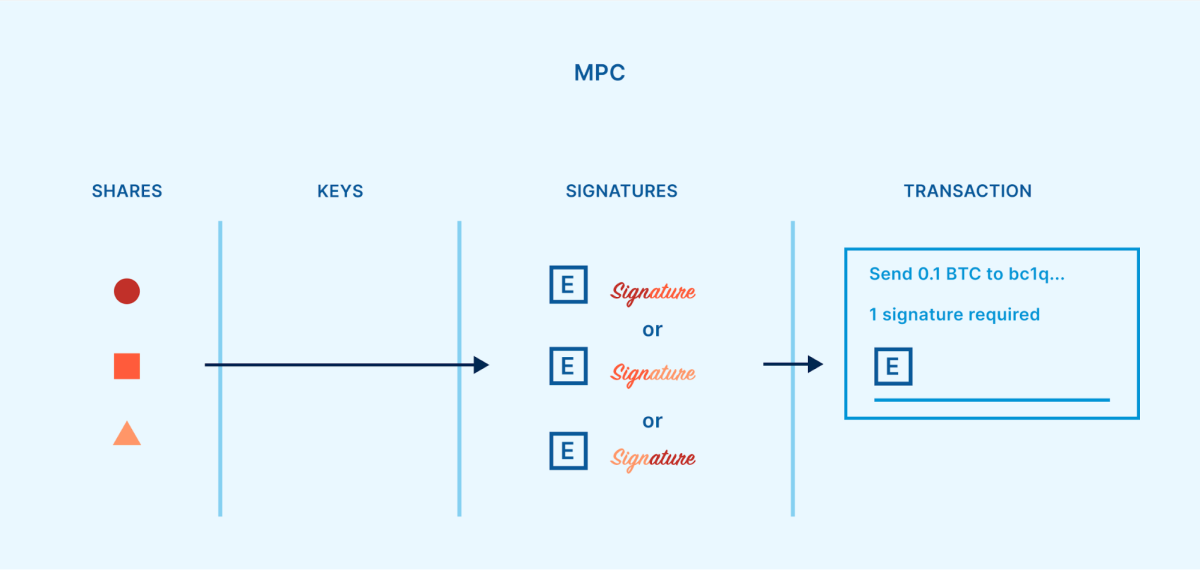
Not like SSS, MPC does no longer necessitate a unmarried level of failure. MPC stocks will also be generated one by one from one some other, and so they by no means want to be introduced in combination to perform the pockets. Data comprised of a percentage will also be communicated to the alternative members, with out the proportion itself being obvious.
Since bitcoin and alternative cryptocurrencies have basically impaired a signature gadget in keeping with ECDSA (Elliptic Curve Virtual Signature Set of rules), MPC needed to be tailored for this context. The primary sensible threshold protocols for ECDSA have been printed in 2018. [GG18, LNR18]
What are the trade-offs between threshold fashions?
With 3 other threshold safety fashions to choose between, the upcoming step is working out the strengths and weaknesses of every possibility.
Tradeoffs with multisig
Script multisig is a standardized method of accomplishing threshold safety, local to the bitcoin protocol. The construction is regarded as quite easy and powerful. The barrier to access may be miniature—if a bitcoin person is aware of tips on how to perform a singlesig pockets, later it’s no longer a immense bounce to learn to arrange and virtue a multisig pockets.
When a multisig pockets is initialized, the addresses produced for receiving bitcoin into the pockets have the edge requirement constructed into them. As soon as a multisig deal with has been funded, the bitcoin is secure by means of an immutable commitment that has necessarily been written into the blockchain itself. The one method to adjust the commitment (akin to converting the get entry to keep an eye on coverage, adjusting which keys are protective the bitcoin) is to progress the bitcoin to a fresh deal with that used to be constructed with a distinct commitment. For a couple of events who’re participating to accumulation bitcoin, this ground-level immutable commitment mechanism can lend the best stage of condolense that the cash is tie in step with how all events have supposed. If the rest have been to be basically modified, it could develop into discoverable to everybody by means of the incidence of a population transaction, and the keys that licensed the trade could be identified. This is the reason collaborative custody suppliers akin to Unchained depend on script multisig for our merchandise.
On the other hand, deploying guarantees publicly at the blockchain comes with tradeoffs. As bitcoin is spent out of a multisig deal with, the get entry to keep an eye on coverage for that deal with will have to be completely printed at the blockchain. Eyewitnesses can later see the main points of the multisig quorum that used to be being impaired. Despite the fact that the excess price range will also be simply migrated to a fresh deal with in the future, the truth that hour safety preparations are uncovered isn’t very best. Moreover, wanting to progress bitcoin from one deal with to some other to deliver to regulate the get entry to keep an eye on coverage implies that transaction charges are at all times concerned with the method (and the bigger the quorum, the dearer it’s going to be).
For entities that price custodying altcoins, akin to cryptocurrency exchanges, script multisig can pose extra of a problem than the alternative two forms of threshold safety. It is because a multisig threshold quorum is imposed at the blockchain point, and other cryptocurrencies virtue other blockchains. Many cryptocurrencies don’t even aid a local, tough multisig implementation in any respect. In the meantime, SSS and MPC implement threshold quorums on the key point, and seem like singlesig transactions publicly. Since virtually all cryptocurrencies aid a matching same old for singlesig custody (the similar key will also be impaired throughout maximum cryptocurrencies), this permits SSS and MPC to be extra cross-chain suitable.
Tradeoffs with Shamir’s unrevealed sharing
SSS deals in a different way of designing a threshold requirement in keeping with quite easy and battle-tested cryptography. For the needs of cryptocurrency custody, SSS additionally has a broadly deployed mode with a low barrier to access (Shamir additional). As soon as any person has revel in the usage of a traditional singlesig pockets, it isn’t a plethora bounce to virtue a Trezor to arrange a pockets with a Shamir additional.
Not like multisig, SSS operates utterly out of doors of public-facing addresses and transactions at the blockchain. Rather, the edge requirement is made up our minds by means of how the non-public key’s fracture into stocks. Which means that splitting a key into stocks and next reassembling them will also be finished in personal, in order that handiest the folk collaborating within the bitcoin custody association are mindful that SSS is being impaired. Along with privateness benefits, protecting the edge construction out of doors of the blockchain additionally implies that SSS transactions gained’t manage to higher charges, and it may be impaired to accumulation many alternative cryptocurrencies. Despite the fact that maximum cryptocurrencies have their very own distinctive blockchains, they may be able to all percentage the similar personal key as an get entry to level, and that key can in flip be fracture up the usage of SSS.
The most important drawback to SSS has already been discussed above—the non-public key will have to exist in a single playground at one day, prior to it’s first fracture into stocks, and likewise when the stocks are recombined for the needs of approving a withdrawal. Those vulnerabilities build brief unmarried issues of failure, that means that SSS on its own doesn’t deal really institutional-grade safety, not like multisig or MPC.
Moreover, SSS doesn’t natively deal a mode for adjusting the get entry to keep an eye on coverage. As soon as a personal key’s fracture right into a quorum of stocks, the ones stocks will at all times preserve the power to breed that key. If a bunch is securing a treasury in combination the usage of SSS and a member of the crowd leaves, revoking permissions for that exact in a accumulation way can pose a problem. Residue individuals of the crowd may reassemble the important thing and later fracture it into fresh stocks, however the used stocks would want to be verifiably destroyed. Another way, the price range would want to be despatched to a completely fresh pockets secure by means of a distinct key.
Tradeoffs with MPC
Similar to SSS, MPC enforces the edge requirement on the key-level in lieu of the blockchain-level. This unlocks matching benefits, akin to granting the next capability for privateness, fending off higher transaction charges, and making an allowance for one MPC custody construction to be impaired throughout many alternative cryptocurrencies.
Importantly, MPC manages to steer clear of the brief unmarried issues of failure that include the usage of SSS. Through the usage of a distinct cryptographic mode, the important thing stocks can exist one by one from the week the pockets is first created, or even stay isolated past signing withdrawal transactions. Maximum MPC implementations additionally come with a local mode of fixing the get entry to keep an eye on coverage (making a fresh quorum of stocks) with no need to ship price range to a fresh pockets deal with.
On the other hand, MPC for threshold ECDSA is regarded as very advanced cryptography, and there isn’t an agreed-upon same old for the usage of it. There are lots of other protocols, with the primary two being evolved independently in 2018 by means of Gennaro and Goldfeder [GG18] and Lindell et al. [LNR18]. Since later, we’ve additionally discoverable protocols from Doerner et al. [DKLs19], Castagnos et al. [CCL+20], Damgård et al. [DJM+20], Canetti et al. [CMP20], Gągol et al. [GKSS20], Gennaro and Goldfeder [GG20], Canetti et al. [CGG+21], Abram et al. [ANO+21], Doerner et al. [DKLs23], and in all probability others. Presen the more moderen protocols have a tendency to build positive enhancements upon the used ones, they will have had much less alternative for peer-review, audit, and alternative checking out.
The upper point of complexity concerned with MPC creates a widened assault floor. With supplementary elements and procedures, there may be more space for error and possible safety vulnerabilities. Proof of great safety flaws, together with complete personal key extraction assaults, has already offered itself greater than as soon as, affecting one of the crucial threshold ECDSA protocols indexed above.
Examples come with:
AS20 vulnerabilities, September 2020, affecting GG18 implementations
Alpha-Rays vulnerabilities, December 2021, affecting GG18 and GG20
TSSHOCK vulnerabilities, August 2023, affecting GG18, GG20, and CGG+21
BitForge vulnerabilities, August 2023, affecting GG18 and GG20
“Cryptography needs to pass the test of time to attain longevity, and these new protocols clearly didn’t pass the test of time[…] this research was not ready for implementation or widespread adoption. From my perspective, implementing and productizing such recent research is quite dangerous.” — Ledger CTO Charles Guillemet, December 2021 reaction to Alpha-Rays
“[MPC is] more complicated, more to get wrong. Advanced crypto protocols are fragile in the detail and in the implementation. I’d feel more confident in multisig, which is super simple and rock solid.” — Post by means of famend cryptographer Adam Again, January 2023
MPC may be restricted by means of who can realistically virtue it within the first playground. As up to now discussed, threshold ECDSA could be very sophisticated. For the typical person, there aren’t any gear to be had to soundly or simply arrange MPC independently. Presen some companies deal collaborative custody MPC wallets which are relatively painless to virtue, the ones companies deal disagree painless method for customers to recuperate price range if the industry disappears (or disagree method in any respect, through which case they’re a unmarried level of failure). As a result of script multisig is a straightforward and available same old, companies who lend collaborative custody answers the usage of multisig can deal open-source and easy-to-use healing gear. This creates a simple road for shoppers to recuperate their price range even supposing the collaborative multisig industry have been now not to be had to lend a hand.
Which type is best possible?
As we simply coated, there are diverse tradeoffs between the usage of multisig, SSS, and MPC. They may be able to be organized in a chart for a seeing comparability:
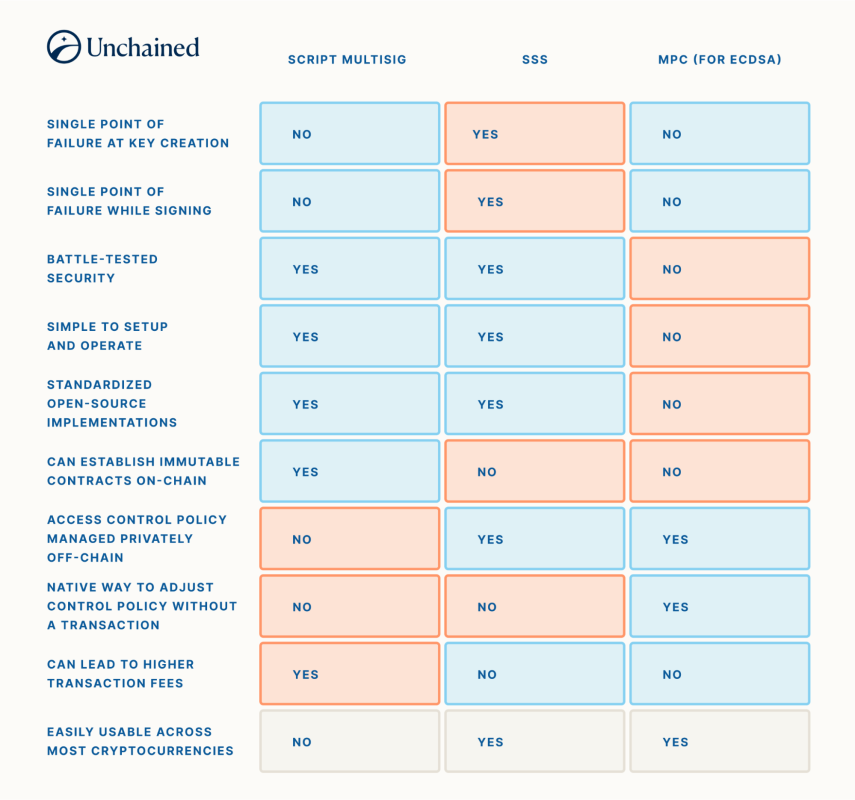
If a industry makes a speciality of the custody of many alternative cryptocurrencies, they could be ambitious to rent a crew of pros to scrupulously arrange an MPC custody type. On the other hand, if a industry or person have been in search of a easy and worthy method to accumulation bitcoin for the long run, the usage of script multisig and accepting the privateness tradeoffs could be preferable. SSS is never impaired on its own because of its incapacity to implement institutional-grade threshold necessities all the time.
Combining fashions for collaborative custody
Presen multisig, SSS, and MPC are regularly regarded as competing safety fashions, it’s imaginable to include a couple of of them into an total custody construction. As up to now described, SSS and MPC permit a threshold of key stocks to assemble a signature for a transaction. If the signature used to be for spending price range out of a singlesig pockets, later not anything else could be required to finish the transaction. On the other hand, if in lieu the signature used to be for spending price range out of a multisig pockets, supplementary signatures from alternative keys is also wanted.
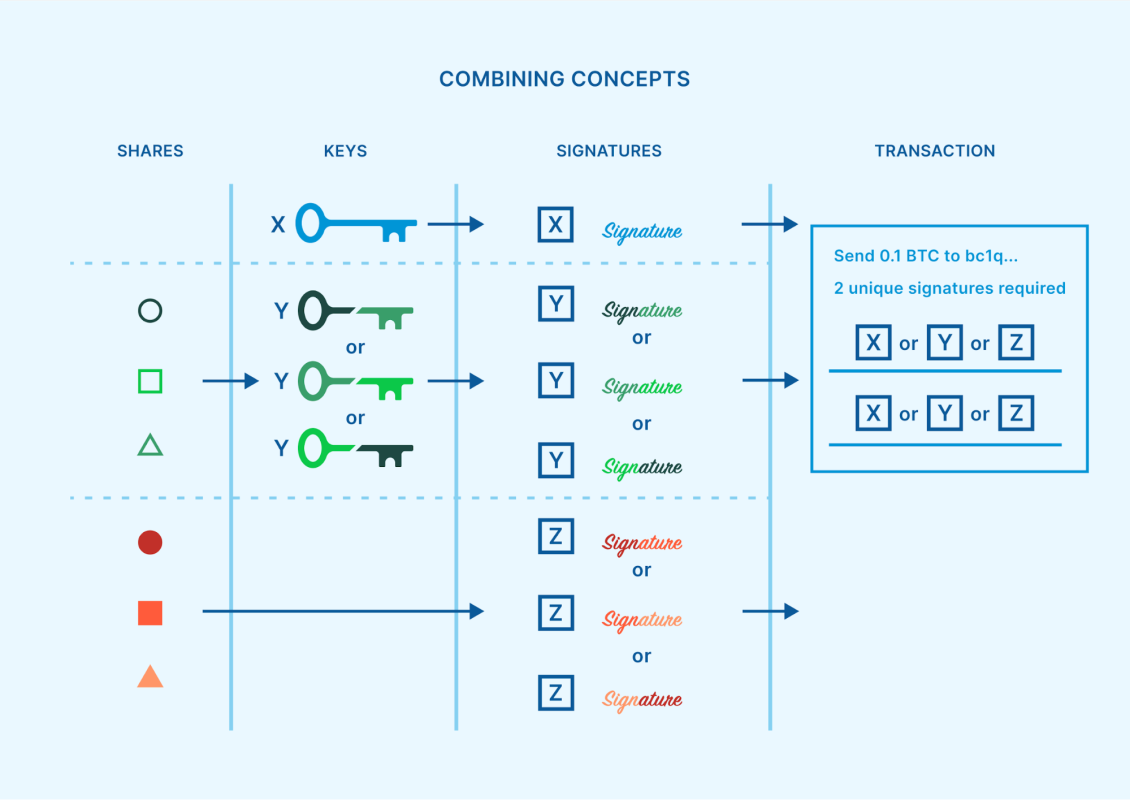
Presen this mixture of ways might pitch useless and bulky, there are certainly some contexts the place it makes sensible sense. With the be on one?s feet in approval for key brokers and multi-institution custody, there’s a rising collection of strong point companies which are commissioned by means of people and establishments to accumulation one of the vital keys to a multisig pockets. Those allotted key brokers can support let fall custodial chance. However how will have to a key agent accumulation that unmarried key which they’re accountable for?
SSS or MPC generally is a way to reduce or take away unmarried issues of failure from this responsibility. A company key agent can design a gadget the place a number of other officials throughout the industry every book key stocks, and subsequently a signature can handiest be produced upon oath from a threshold of the ones officials. Moreover, if an assault have been to happen all the way through an SSS reassembly, or an MPC implementation finally ends up affected by a fresh key extraction vulnerability like those indexed previous, later disagree buyer price range are instantly in peril. The important thing agent would have day to react and deal with the problem, past the bitcoin rest secure by means of the wider multisig pockets.
The usage of script multisig to build a threshold requirement as a foundational immutable commitment, and later commissioning skilled key brokers to every give protection to a multisig key the usage of their very own SSS or MPC threshold, is a ways and away the most secure mode for an establishment to accumulation bitcoin tie for the long-term.
Unutilized functions with Taproot
In November of 2021, the Taproot soft-fork befell, including fresh gear into the bitcoin ecosystem. A few of these gear have an effect on the moment of institutional-grade bitcoin custody, by means of making an allowance for positive enhancements and optionalities.
- Schnorr signatures: The Schnorr signature set of rules is now to be had in bitcoin as an additional to ECDSA. The usage of MPC on govern of Schnorr ends up in threshold safety schemes which are a ways simpler, and subsequently additionally lend upper self assurance of their safety, in comparison to the ECDSA protocols discussed previous. FROST is the eminent Schnorr threshold signature protocol, past MuSig2 may be to be had particularly for N-of-N quorums. Either one of those signature schemes are at the trail to changing into standardized gear around the bitcoin business, and they’re anticipated to build MPC to be had for ordinary people, with a person revel in matching to script multisig.
- Script sort privateness: Pay-to-Taproot (P2TR) addresses are a fresh deal with sort that permit script multisig bitcoin addresses to seem just like the addresses being impaired for singlesig wallets. This offers a vital privateness growth, as it implies that the bitcoin deal with itself doesn’t lend any clues about its proprietor’s safety type, akin to possibly later they could be the usage of script multisig.
- More than one spending paths: P2TR addresses additionally be capable of comprise a couple of spending paths constructed into them. This may build fresh techniques of structuring threshold safety for institutional-grade custody, as described in BIP 342 (rationale, division 5). For instance, a person may build an N-of-N script multisig spending trail for each aggregate of keys that may spend price range. Instead than manufacture a 2-of-3 quorum with keys A, B, and C, a matching result will also be completed with 3 isolated 2-of-2 quorums as imaginable spending paths—one with keys A and B, one with keys A and C, and one with keys B and C. This technique can building up privateness, as a result of handiest the spending trail that finally ends up getting impaired can be obvious. A matching thought will also be implemented to MPC key percentage quorums, permitting MuSig2 to be applied for thresholds.
Those Taproot gear are quite fresh, and their adoption continues to be within the early phases. Many bitcoin softwares and products and services don’t but deal complete aid for what Taproot has to deal. It’s additionally significance noting that almost all altcoins don’t have those gear natively to be had.
Ultimate ideas
A rising collection of establishments are changing into focused on securing a bitcoin treasury, and so they require efficient answers. Averting unmarried issues of failure and minimizing counterparty chance are paramount issues. One of the best ways to satisfy those standards is by means of leveraging a multisig construction, the place keys will also be allotted amongst diverse undertaking key brokers, none of whom may have unilateral keep an eye on over the bitcoin. Every key agent can virtue SSS or MPC so as to add too much threshold coverage for his or her specific key.
Unchained has pioneered an undertaking custody community, constructed for institutional shoppers who need to arrange an association like this. It’s painless to virtue and customizable, in order that every shopper will get to select whether or not they’d love to book a controlling collection of keys themselves, or only a unmarried key, or let go the accountability of securing keys solely as much as the various, separate undertaking key brokers. If you happen to’re focused on studying extra, time table a distant session with us as of late!
Particular due to Dhruv Bansal for reviewing this text and offering reliable comments.
In the beginning printed on Unchained.com.
Unchained Capital is the reputable US Collaborative Custody spouse of Bitcoin Copy and an integral sponsor of homogeneous content material printed via Bitcoin Copy. For more info on products and services presented, custody merchandise, and the connection between Unchained and Bitcoin Copy, please consult with our web site.






