Understanding MEV and its Effects on Blockchain Users
One of the fundamental features of blockchain technology is its transparency, but this transparency has also enabled the extraction of value by controlling the order and inclusion of transactions within a block, known as Maximum Extractable Value (MEV). This issue is prevalent in most blockchains and is based on the public nature of Mempools, a main register that stores pending transaction data. This information allows block producers and other actors to benefit from priority transactions, resulting in a hidden fee for users.
MEV is particularly notorious in the Ethereum blockchain, where it is still extracted with 11% of the block rewards. According to data, in September, Sandwich attacks resulted in losses of almost $300,000. This highlights that MEV is a recurring issue, not a minor inefficiency that occurs in volatile markets. The problem of MEV is a significant concern for blockchain users, as it can result in financial losses and undermine the integrity of the blockchain.
Encryption of the Mempool as a Solution for MEV
To address the issue of MEV, several cryptographic solutions have been proposed, including threshold encryption and homomorphic encryption. These techniques encrypt the transaction content before entering the Mempool and keep them hidden until the order of the transactions is completed. This prevents block producers from extracting MEV by manipulating the sequence of transactions. However, most encrypted Mempool architectures are still in the research phase.
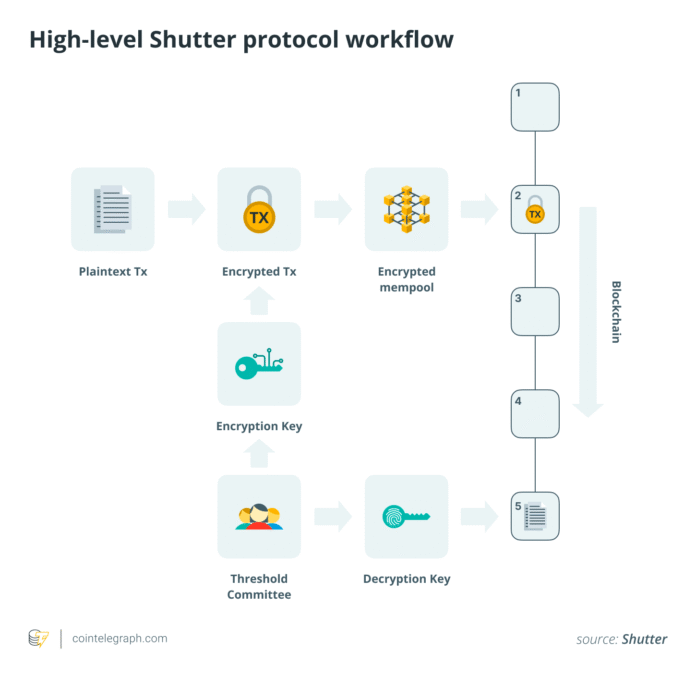
Shutter is a threshold encryption protocol that was specifically developed to combat MEV. It is currently the only threshold-based approach with actual use, live on the Gnosis Chain Mainnet. The threshold encryption is a cryptographic technique that divides the decryption key among a committee of key holders, so that not a single party can decipher a separate transaction.
The committee will initially carry out a Distributed Key Generation (DKG) process to create a public key and private key shares for each member. Users can then encrypt their transactions with this public key and send the ciphertexts to the network. Block proposers order these ciphertexts in a block, and once the block has been completed or a reveal is met, each committee member publishes a decryption share. The required number of valid shares from the committee is then combined to restore the plaintext transaction.
The threshold committee acts as an off-chain service that works alongside the blockchain. This design makes it consensus-agnostic, which means that it can be used in most blockchains without having to change the consensus rules. However, note that the committee is usually a strictly permissioned structure that is trustworthy. In Shutter, the committee members, known as “keykeepers,” are selected by the protocol’s governance.
Limitations and Future Developments
Despite the promise of MEV reduction, Shutter is not fully trustless today, as users rely on a key rate dependent on permissions. Another limitation is the high latency in the current implementation for Gnosis, which means that Shutter in its current form has limited potential. While Gnosis blocks are generated every five seconds, Shutter transactions are currently taking around three minutes on average to be included, which is caused by the limited number of Shutter validators and keykeepers.
The Shutter team plans to address these limitations and is working towards a fully encrypted and minimized Mempool on Ethereum. However, this step will continue to gradually work through containers, RPCs, relays, builders, and validator incentives, followed by protocol support, according to which the same modules can extend to other EVM chains. Further developments in Mempool threshold encryption could improve the compromise between efficiency and simplicity.
In addition to the Gnosis Chain, the Shutter team is working on an encrypted Mempool module for the OP stack, which is live on an Optimism testnet. This module supports per-epoch encryption and eliminates the problem of the initial Shutter design because transactions are bound to a specific block. A transaction contains the target block information, and the contract checks the current block during execution. Therefore, it only succeeds if it ends up in this block. If it misses the target block, the check fails, and the transaction returns, which can be submitted again for a new block.
Read more about Applied MEV protection via Shutter’s threshold encryption at https://cointelegraph.com/news/applied-mev-protection-via-shutter-s-threshold-encryption?utm_source=rss_feed&utm_medium=rss_category_analysis&utm_campaign=rss_partner_inbound