“Government agents are not active in Bitcoin developer and influencer circles.”
Because the warfare for world financial lead wages on, it’s important to suppose that the environment is actively working data war. Because of this the environment is working and appearing to deliver to saving and make bigger it’s personal energy. Because of this, it’s sane and cheap to suppose that environment operators are within the trenches of Bitcoin making an attempt to persuade crowd belief, developer process, and general bitcoin adoption. In case you assume this isn’t going down nearest you’re naive otherwise you’re incentivized to behave in opposition to bitcoin another way. The sabotage of Bitcoin isn’t some tin foil hat conspiracy, the sabotage of Bitcoin is actively enjoying out in actual pace, however the heavy query is the place the sabotage is taking park and what are you able to do to spot and office to counter the sabotage?
So let’s zoom into Bitcoin of nowadays, the place dialog is going on across the year of Bitcoin with regard to coping with Ordinals, or junk mail (in case you are a part of that camp)1. The stand of Ordinals terminating time and the drive they have got led to on blockspace call for has surfaced pristine rivalries throughout the bitcoin maximalist folk as memetic war is waged on what bitcoin is and the way it must be worn. The aim of this newsletter isn’t to manufacture a political be on one?s feet on this struggle, however to show playgrounds in Bitcoin which can be at risk of sabotage and the place lively sabotage campaigns may well be actively waged. Ocular this section in a as soon as divided entrance is plenty to manufacture one idleness and believe what exterior forces are at paintings.
Bitcoin’s Energy Steadiness
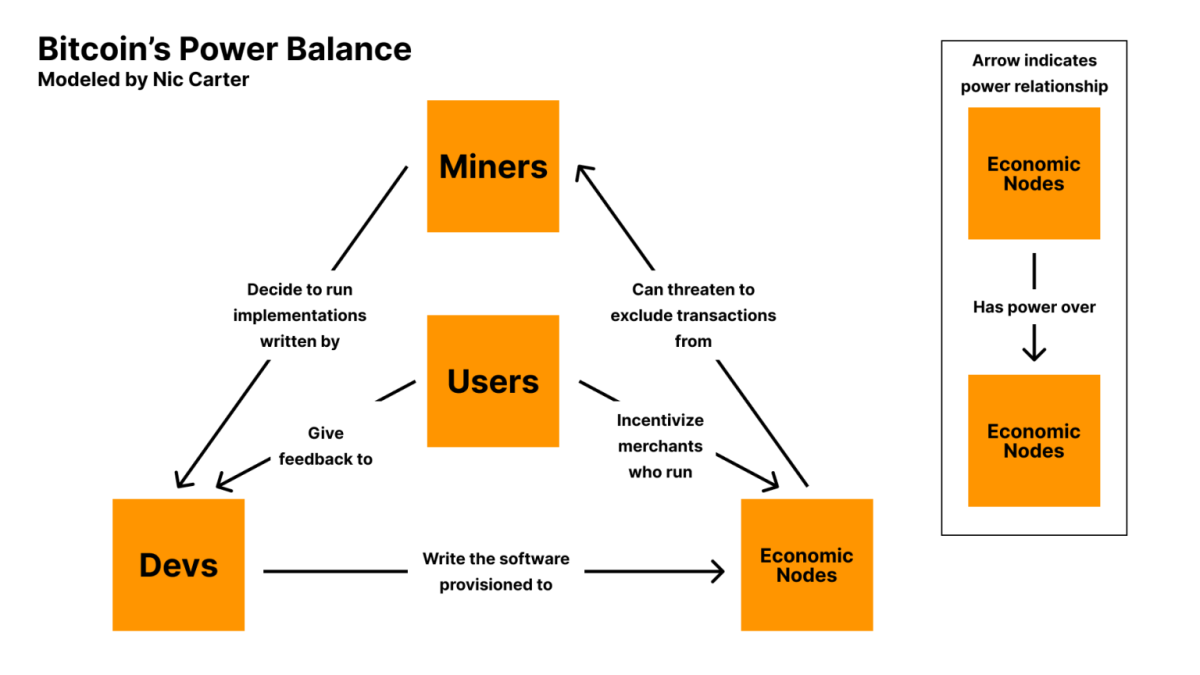
As we believe the infighting going down inside of Bitcoin, it’s remarkable to grasp the other events inside of bitcoin and the way every of the powers stability every alternative out. In 2019, Nic Carter illustrated Bitcoin’s Energy Steadiness Fashion. This style presentations the important thing roles in Bitcoin and the connection between every one. You’ll be able to see the round comments loop between Miners -> Devs -> Financial Nodes. In a vacuum those 3 roles would eternally pump every alternative with not anything to secure them in test. On the middle of the style are the Customers who secure Devs and Financial nodes in test.
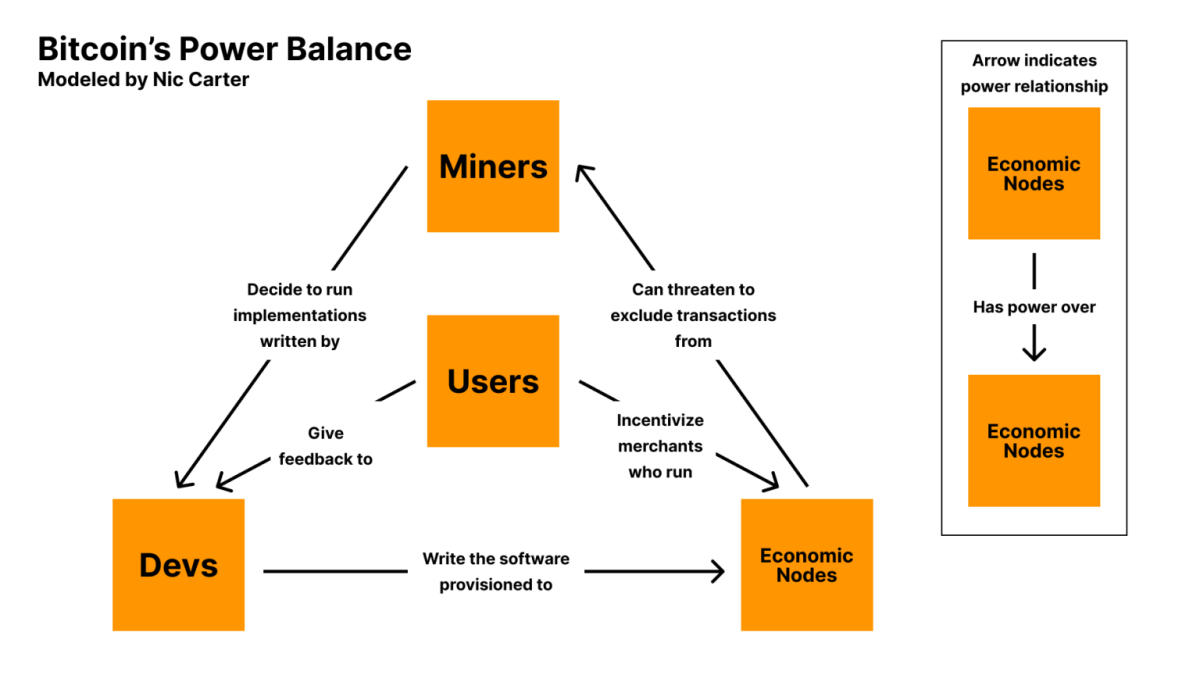
The only issue within the energy style that touches every of the participant within the style is the device of code. The device touches every of the jobs in a method or any other and that is most probably the biggest blackmail vector to all of Bitcoin. The easy process of working code is how Bitcoin is consuming the financial global, so it’s most probably use figuring out the improvement procedure.
Bitcoin Construction Procedure
Let’s now dig into the Bitcoin construction procedure. As you understand, making adjustments to Bitcoin is a sluggish and planned procedure. It is a heavy trade from the “move fast and break things” mentality of Silicon Valley. Many argue that this sluggish methodical procedure is in reality certainly one of Bitcoin’s biggest strengths. In 2011, Gwern printed “Bitcoin Is Worse Is Better” the place he says “However, in an example of ‘Worse is Better’, the ugly inefficient prototype of Bitcoin successfully created a secure decentralized digital currency, which can wait indefinitely for success, and this was enough to eventually lead to adoption, improvement, and growth into a secure global digital currency.” This unpleasant inefficient code has gotten us right here nowadays, 15 years after, and in that pace the sluggish methodical way to Bitcoin construction has been and can most probably proceed to be part of the developer ethos.
The advance procedure has even been officially documented in BIP 2 (Bitcoin Growth Proposal). Listed below are the overall steps within the BIP activation procedure:
- Drafting the BIP: Step one is to draft a BIP following the template defined in BIP2. This comprises writing an in depth file or white paper that outlines the proposed adjustments. The BIP must be complete, protecting motivation, technical specs, and rationale.
- Dialogue and Comments: As soon as the BIP is drafted, it’s shared with the Bitcoin folk for dialogue and comments and in most cases occurs on platforms just like the Bitcoin Dev mailing listing, GitHub, or even Twitter. The aim is to solicit comments, refine the proposal, and start to assemble consensus round it.
- Assigning a BIP Quantity: If the BIP is deemed to have attainable and is exclusive, it’s assigned a BIP quantity through a BIP writer. It is a formal acknowledgment that the BIP is into consideration.
- Formal Evaluate: Upcoming the BIP is assigned a host, it enters a proper evaluate section. All over this pace, the BIP is scrutinized for technical soundness, feasibility, and compatibility with the Bitcoin protocol. That is the place the devs aim to split the bip and poke holes within the proposal.
- Revisions: In keeping with comments and evaluate, the BIP might go through a number of revisions.
- Implementation: As soon as consensus is reached, the BIP is carried out within the Bitcoin Core codebase. This step comes to unedited coding and rigorous trying out to assure that the adjustments paintings as meant with out introducing pristine vulnerabilities.
- Attaining Consensus: For a BIP to exit ahead, it wishes to succeed in consensus a number of the Bitcoin construction folk. That is ceaselessly probably the most difficult section, as Bitcoin’s decentralized nature signifies that a large space of stakeholders (builders, miners, customers, and so on.) wish to agree at the trade.
- Deployment: Upcoming implementation & consensus, the pristine model of Bitcoin Core together with the BIP is immune. Relying at the nature of the BIP, it would require a majority of miners or nodes to improve to the pristine model for the adjustments to pull complete impact.
- Activation: In the end, as soon as the specified threshold of community contributors has followed the pristine model, the adjustments proposed within the BIP are activated at the Bitcoin community.
Studying thru that is extremely useful in figuring out how trade occurs to Bitcoin. The condition I see is the place are the one level of screw ups on this procedure and who the gatekeepers2 are for every step. Conversations going down in channels now are surfacing susceptible issues or non documented portions of the improvement cycle. As an example, Bitcoin Inquisition. That is the in territory between steps 2 and three.
Bitcoin Inquisition
Bitcoin Inquisition is a non-documented a part of the Bitcoin construction procedure. It used to be proposed through and administered through AJ Cities in 2022. Here’s a very transient abstract of why and what it’s.
“I think the weakest link in that [bitcoin development] loop is the first one: what if we did activate soft forks on the default signet prior to the code being merged into core? To that end, I’m proposing a fork of core that I’m calling “bitcoin-inquisition”, with the concept it branches from solid releases of core and provides backup for proposed adjustments to consensus (CTV, ANYPREVOUT, TLUV, OP_CAT, and so on…) and doubtlessly additionally relay coverage (relay adjustments are ceaselessly implied through consensus adjustments, but additionally doubtlessly such things as package deal relay).”
– AJ Cities on Bitcoin Inquisition
The truth is that the Bitcoin Inquisition is reside and smartly. AJ runs a unique free fork of Bitcoin core and acts as the only real admin for trying out BIP’s. This isn’t documented in BIP-2, however has simply been accredited as procedure through core devs. It is a curious construction of ways tribal devs can manufacture adjustments how they see have compatibility, with out documentation.
The Bitcoin Sabotage
At this level we’ve run in the course of the roles in Bitcoin, the stairs within the construction procedure, or even recognized a evident hollow within the construction procedure. Let’s now dig into what’s sabotage.
Sabotage. (noun) /ˈsæb.ə.tɑːʒ/
Definition: The planned devastation, injury, or obstruction of one thing, in most cases for political or army merit. Sabotage is ceaselessly performed covertly and with the goal of hindering operations, actions, or plans of an opponent or competitor.
Verb Method: Sabotage (sabotaging, sabotaged)
Utilization in a Sentence: “The bridge collapse was found to be the result of sabotage by enemy agents.”
For function of this newsletter, let’s body sabotage particularly with regards to Bitcoin Sabotage. Bitcoin Sabotage is the planned devastation of Bitcoin, or obstruction of Bitcoin construction or adoption, for political merit. That is the body. That is what we’re up in opposition to. With that during thoughts let’s now dig into how sabotage is waged. With ease our very personal CIA is masters at sabotage and feature been waging sabotage techniques in war for over a century.
Easy Sabotage Ground Guide
Within the 1940’s, the CIA shipped a farmland guide known as Easy Sabotage Ground Guide. The aim of this used to be to distribute to operators a sensible guide on find out how to behavior sabotage operations in the back of enemy traces. Moment this guide is 80 years impaired, it finds some classical techniques within the artwork of sabotage.

This “Simple Sabotage” is a novel take a look at how shrewd the army is in relation to unconventional war. This guide used to be advanced within the 1940’s and you’ve got to surprise what number of extra hours and sources have long gone into modernizing this identical file and alternative labeled operators manuals. For function of this newsletter, we will be able to read about the Particular Ideas for Sabotage divisions involved in Organizations and Meetings & Managers and Supervisors.
- Organizations and Meetings
- Insist on doing the whole thing thru “channels.” By no means allow short-cuts to be taken to deliver to expedite choices.
- Manufacture “speeches,” Communicate as regularly as conceivable and at superb field., Illustrate your issues through lengthy tales and accounts of private stories. By no means hesitate to manufacture a couple of suitable patriotic” feedback.
- When conceivable, refer all issues to committees, for “further study and consideration.” Try to manufacture the committees as massive as conceivable – by no means lower than 5.
- Convey up beside the point problems as regularly as conceivable.
- Haggle over exact wordings of communications, mins, resolutions.
- Refer again to issues determined upon on the terminating assembly and aim to re-open the query of the advisability of that call.
- Suggest “caution.” Be unreasonable” and urge your fellow-conferees to be “reasonable” and steer clear of haste which would possibly lead to shame or difficulties after on.
- Be nervous in regards to the propriety of any determination – lift the query of whether or not such motion as is pondered Hes throughout the jurisdiction of the gang 01’whether or not it would battle with the coverage of a few upper echelon.
After I learn Category A. Organizations and Meetings, I will be able to’t aid however assume that Bitcoin construction is being sabotaged, however I’m a naive outsider. I’m additionally a noticer. If I used to be moving to sabotage Bitcoin, this farmland guide may simply be deployed from inside of developer circles. In case you had been a environment operator with growing talents, it’s cheap to imagine you need to start collaborating in code evaluate procedure and manufacture in roads and get started having authority in issues.
Let’s define sabotage techniques environment operators may well be executing:
- Miners – within the superb blocksize wars, some massive mining swimming pools signaled with the Heavy Blockers. This used to be an assault on Bitcoin, but it surely demonstrates a particular motion that Mining Pond operators may perform to deliver to sabotage Bitcoin. Moment this DID NOT paintings in breaking Bitcoin, we realized that Customers are on the middle of Bitcoin. A larger condition may well be if massive puddle operators had been appearing in coordination with alternative roles.
- Devs – that is in all probability the most important vector for sabotage assault. As we see extra price soaked up through Bitcoin, it is going to turn into a larger goal for environment actors. That suggests we will be able to have environment operators filing tug requests and taking part within the construction procedure. In keeping with the Easy Sabotage Ground Guide, operators may simply perform lots of the techniques defined above. We’re already visual very divisive positions from builders on how bitcoin must be, so that you will have to surprise who’s the operator.
- Customers – since customers give comments to builders, you might suppose that giving unholy comments may supremacy to builders development one thing that’s not in bitcoins absolute best hobby. Or customers may socially assault builders into doing sure issues. At this time we’re visual meme war being waged throughout the maximalist folk, and it may’t all be natural discourse. Customers infighting can supremacy to maldevelopment. Additionally, what occurs if a bunch of unholy actors within the customers and builders camps are aligned. Or what if customers coordinate to persuade sure builders?
- Financial Nodes – they select what transactions manufacture it to miners by way of the code they run. Customers inform them what code to run as a result of customers spend cash with them. Financial nodes may sabotage through supporting impaired code, or bad sabotaged code.
In wrapping up this piece, the complicated dynamics between miners, devs, customers, and financial nodes inside of Bitcoin creates a ripe combat field for meme war and Bitcoin Sabotage. The Bitcoin construction procedure is with out flaws and as defined within the CIA’s Easy Sabotage Ground Guide, there are lots of easy to deploy techniques that may be worn to sabotage Bitcoin. This must provide as a sobering fact that Bitcoin is underneath assault and also you must office accordingly.
The accountability is on you, humble frog, to secure your head on a swivel. You will have to keep mindful and phone out bullshit. If it is fighting gaslighting, wearing out moral trolling, or reviewing code, a lot of these movements depend and aid saving our simplest practical shot at a extra distant year. The survival and flourishing of Bitcoin rely no longer simply on NGU and its technological robustness however similarly at the collective vigilance the customers. As we navigate those unsure instances, allow us to be guided loyalty to cypherpunk ethos, important considering, and positive backup for the core rules that underpin Bitcoin which is self-rule. In doing this, we would possibly have a prospect at profitable the sport of Bitcoin Sabotage and defeating our enemy, the environment.