DeadLock Ransomware: A New Threat that Exploits Polygon Smart Contracts
Cybersecurity researchers have discovered a new ransomware variant called DeadLock, which utilizes Polygon smart contracts to maintain its infrastructure and evade traditional detection tools. According to a recent report by threat intelligence firm Group-IB, DeadLock has been largely under the radar due to its lack of a publicly available affiliate program, data leak site, and limited confirmed victims.
First observed in July 2025, DeadLock has been found to use a sophisticated strategy that involves deploying smart contracts on the Polygon network to store and rotate proxy server addresses. These proxies act as intermediaries between infected systems and the ransomware operators, allowing command-and-control traffic to move endpoints without relying on a centralized infrastructure that can be seized or blocked.
How DeadLock Hides Ransomware Infrastructure in Polygon Smart Contracts
Group-IB’s analysis reveals that DeadLock uses smart contracts to store and rotate proxy server addresses, which are then retrieved by the malware through a simple read operation that leaves no obvious transaction footprint and incurs no network costs. This technique is similar to previous campaigns, such as EtherHiding, where North Korean threat actors used the Ethereum blockchain to hide and spread malware payloads.

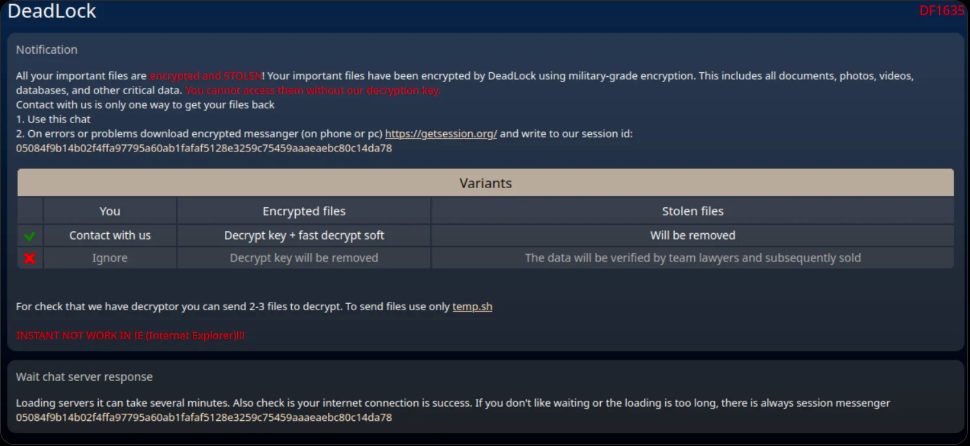
Once deployed, DeadLock encrypts files and appends the “.dlock” extension, changes system icons, and replaces the victim’s wallpaper with ransom instructions. The group’s ransom notes have evolved over time, with the first copies referring only to file encryption, while later versions specifically stated that sensitive data had been stolen and threatened to sell it if payment was not made.
This Ransomware Doesn’t Just Lock Files – It Opens a Chat with Hackers
Group-IB identified at least three different DeadLock samples starting in mid-2025, each showing incremental changes in tactics. Analysis of the associated PowerShell scripts suggests that the malware aggressively disables non-essential services, deletes volume shadow copies to prevent recovery, and whitelists a limited number of processes, particularly AnyDesk.
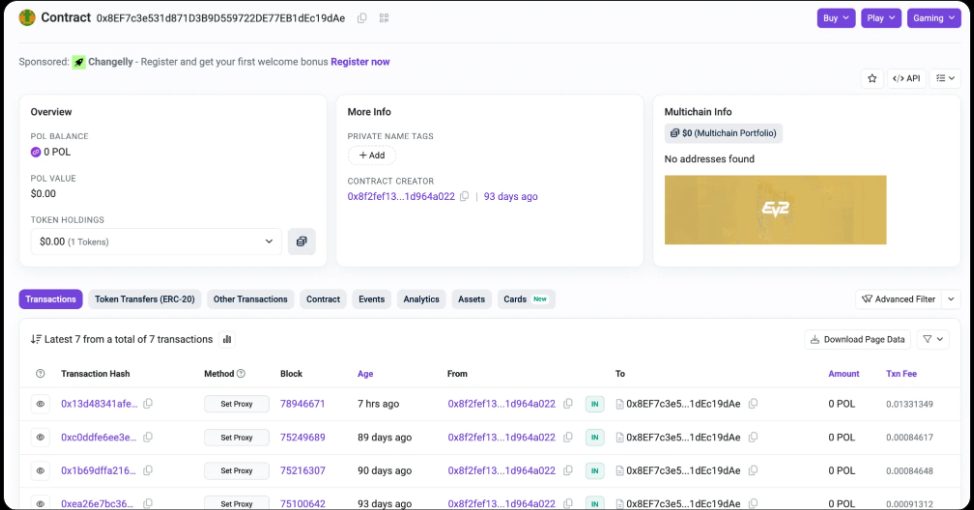
A key element of how DeadLock works is an HTML file placed on infected systems that embeds an encrypted session messenger interface. Victims can communicate directly with attackers through this file without installing additional software. The embedded JavaScript retrieves proxy addresses from the Polygon smart contract and then forwards encrypted messages through these servers to a session ID controlled by the ransomware operators.
For more information on the DeadLock ransomware and its exploitation of Polygon smart contracts, visit https://cryptonews.com/news/deadlock-ransomware-polygon-smart-contracts-exploit/

