Understanding the Trust Wallet Hack: Key Insights for Crypto-Friendly SMBs
The recent Trust Wallet hack, which resulted in a loss of approximately $7 million, has provided valuable security insights for small and medium-sized businesses (SMBs) that use cryptocurrencies. Although Trust Wallet primarily serves individual users, the attack’s mechanics highlight common vulnerabilities that also affect crypto-friendly SMBs, including fintech companies and decentralized autonomous organizations (DAOs).
The incident has sparked concerns about the distribution and update mechanisms of cryptocurrency tools, with experts noting that browser extensions, APIs, and external libraries are widely used in cryptocurrency payroll systems, treasury management, and fintech services aimed at SMBs. In this article, we will delve into the details of the Trust Wallet hack, its impact on the crypto community, and the challenges the wallet faced during the compensation process.
What Happened in the Trust Wallet Hack?
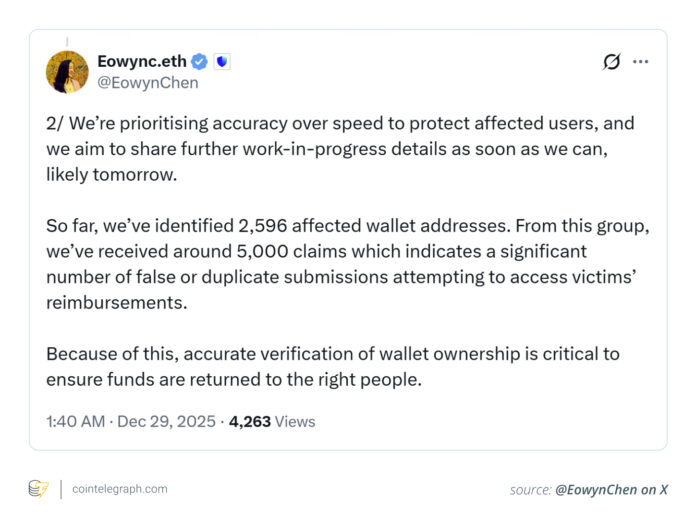
On December 24-26, 2025, attackers targeted Trust Wallet’s Chrome browser extension by distributing a malicious update that affected users running version 2.68. The attack resulted in the theft of approximately $7 million worth of cryptocurrencies and affected 2,596 verified wallet addresses. Nearly 5,000 refund requests were later submitted by users.
Security experts discovered that attackers had injected malicious JavaScript into the extension, allowing them to steal recovery phrases and private keys during normal wallet usage. The attack likely involved a stolen Chrome Web Store API key, which allowed the malicious update to be distributed through official channels rather than relying solely on phishing.

Immediate Impact on the Cryptocurrency Community
The Trust Wallet hack briefly weakened trust in browser-based wallets, with experts noting that many victims were unaware that browser extensions act as hot wallets, exposing them to malware and supply chain threats despite their convenience. The attack also renewed the debate over self-custody, with many commentators pointing to hardware wallets and offline storage as lower-risk options, particularly for larger holdings.
Beyond Trust Wallet, the attack sparked broader concerns about the distribution and update mechanisms of cryptocurrency tools. The case showed that risks outside of a company’s core systems can still cause significant damage, highlighting the importance of addressing vulnerabilities before incidents occur.
The Process of Reviewing and Processing Claims
An important insight from the Trust Wallet hack became clear in the post-attack phase. Nearly 5,000 applications were submitted for just over 2,500 affected addresses, highlighting the risk of duplicate, incorrect, or fraudulent submissions. Without robust verification procedures, refund processes can become overwhelmed, delaying legitimate payments and increasing operational risk.
Trust Wallet required applicants to submit wallet addresses, transaction records, attacker addresses, and other supporting details to verify losses. For SMBs, the lesson from the Trust Wallet hack is clear: verification processes must be prepared in advance and not developed during an incident.
Vulnerabilities SMBs Face in Crypto Hacks
SMEs often operate in environments where a single oversight can result in significant asset losses. Threat actors are exploiting the following vulnerabilities in these organizations:
Supply chain and update risks, over-reliance on hot wallets, and social engineering and phishing follow-up are some of the key vulnerabilities that SMBs face in crypto hacks. The Trust Wallet hack exposed the risks of storing large amounts of cryptocurrencies in hot wallets, and the importance of implementing robust security measures to prevent such attacks.
Security Measures for Crypto-Friendly SMEs
In light of the Trust Wallet case, SMBs can take various security measures to protect themselves from similar attacks. These include using cold storage for large assets, implementing mandatory Multi-Factor Authentication (MFA), preparing incident response plans, conducting external security checks, and implementing strong access controls and supplier monitoring.
Training users and employees to recognize phishing attempts and fake messages can also prevent additional losses during high-stress incidents. By implementing these security measures, SMBs can reduce their risk of falling victim to crypto hacks and protect their assets and reputation.
Regulatory Environment After the Hack
Although no immediate regulatory action followed the Trust Wallet incident, it came against a backdrop of stricter global oversight of the crypto sector. Regulators increasingly expect companies to implement strict controls in the areas of custody, incident reporting, and consumer protection.
For crypto-friendly SMBs, this means that security deficiencies can lead not only to reputational damage but also to compliance-related consequences. Compliance with regulatory expectations has become as important for SMEs as maintaining technical resilience. By prioritizing security and compliance, SMBs can build trust with their customers and stakeholders and operate successfully in the crypto space.
Read more about the Trust Wallet hack and its implications for crypto-friendly SMBs at https://cointelegraph.com/news/trust-wallet-s-7m-hack-shows-where-crypto-friendly-smes-may-be-vulnerable?utm_source=rss_feed&utm_medium=rss_category_analysis&utm_campaign=rss_partner_inbound